How to Protect My Company from Social Engineering Attacks?

Social engineering is one of the most significant threats to businesses today. Instead of attacking computer systems, cybercriminals attack the people who use them. They use tricks, fake stories, and manipulation to make employees reveal confidential information or perform harmful actions. To keep your company safe, it is essential to understand how these attacks work and take the necessary steps to protect your team and data. This guide explains what social engineering is, its common types, warning signs, and effective ways to defend your business.
What Is a Social Engineering Attack?
Social engineering is a method hackers use to trick people into revealing private information, giving access to systems, or transferring money. These attacks rely on human psychology, rather than technical weaknesses.
Attackers exploit trust, curiosity, and fear. For example, an email from a CEO or IT department may require a password reset or an emergency payment. When an employee responds, the attacker gains control.
Why Social Engineering Is So Dangerous
Social engineering attacks are effective because they target humans, not machines. Even heavily protected companies may suffer damage due to minor mistakes by their employees.
1. People Are Easier to Trick Than Computers
Hackers know it's easier to deceive employees than to break through firewalls. They know that people click emails quickly and trust familiar logos.
2. One Mistake Can Lead to Major Loss
A single incorrect click can result in the leakage of sensitive data, financial loss, or damage to a corporation's reputation.
3. Attacks Are Becoming Smarter
Attackers collect personal information from LinkedIn, corporate websites, and social media to create authentic messages. You can even impersonate management with fake voices and deepfake videos.
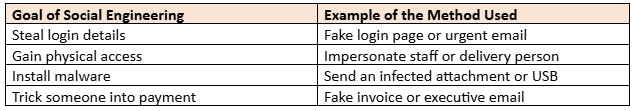
Common Types of Social Engineering Attacks
Typical methods for cybercriminals targeting companies:
1. Phishing
Generate harmful links and attachments to authentic emails and messages. There are frequent cases of sending from banks, government agencies and corporate executives.
Signs of phishing emails:
- Urgent language ("Your account will be locked!")
- Suspicious links or attachments
- Unfamiliar sender addresses
2. Spear Phishing
A more targeted version of phishing aimed at specific employees or executives. The message appears personal and convincing because the attacker has conducted thorough research on the target.
3. Pretexting
The attacker creates a false reason ("pretext") to gain trust, for example, pretending to be from IT support and asking for login details.
4. Baiting
This involves offering something tempting, such as a free download or USB drive, that installs malware when used.
5. Tailgating
A physical form of attack. The attacker follows an employee into a restricted area by pretending to be a visitor or delivery worker.
6. Quid Pro Quo
The attacker promises something in exchange, for example, offering "free software help" if the user turns off antivirus protection.
Warning Signs of a Social Engineering Attempt
Recognizing warning signs is one of the best defences. Train your team to watch for these clues:
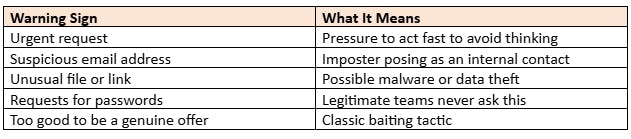
If something feels off, it probably is. Employees should report suspicious messages instead of responding or clicking anything.
Steps to Protect Your Company
Now that you are aware of the risks, let's review the practical steps to protect your business.
1. Train and Educate Employees
Training is the most vigorous defense against social engineering. Employees should be aware of how to identify fake messages and know what to do if they encounter one.
Tips for strong training:
- Conduct regular cybersecurity workshops.
- Send test phishing emails to measure awareness.
- Encourage employees to verify requests by calling or messaging through official channels.
- Reward staff for reporting suspicious activity.
2. Use Multi-Factor Authentication (MFA)
Even if someone accidentally shares a password, MFA can block attackers. Require employees to use a second verification step (like a phone code or fingerprint).
3. Create and Enforce Security Policies
Every company should have written policies that explain how to handle sensitive information and financial requests.
Example rules:
- Always verify large payments with two approvals.
- Do not share company data on personal devices.
- Visitors must wear ID badges and be escorted at all times.
4. Strengthen Technical Defences
Technology should back up employee awareness.
- Use spam filters to block phishing emails.
- Keep systems up to date with the latest patches.
- Install reliable antivirus and endpoint protection tools.
- Monitor login attempts and device activity for unusual patterns.
5. Limit Access to Information
Not everyone needs access to everything. Apply the "least privilege principle" and give employees access only to what they need for their role. Remove unused or old accounts promptly.
6. Protect Physical Spaces
Protect your office with access control cards, visitor records and surveillance cameras. Alert employees not to leave confidential documents or USBs.
7. Encourage a Reporting Culture
Create an environment where employees can report suspicious emails and incidents with confidence and security. Avoid penalties for mistakes and use incidents as learning opportunities instead.
Real-Life Example: How a Simple Email Caused Big Damage
A finance employee at a mid-sized company received an email that appeared to be from the CEO. It asked her to transfer funds for a "vendor payment urgently." The email was polite and professional, but fake. The employee followed the request without confirming it. The company lost $70,000 to a fraudulent account.
What went wrong?
- The email was not verified.
- There was no policy for double approval of transfers.
- Employees were not trained to spot urgent payment scams.
How could it be avoided?
- Training on phishing recognition.
- Dual approval for all financial transfers.
- Verification via phone before sending funds.
Partner with Professionals for Stronger Protection
While internal efforts are essential, collaborating with experts can enhance your security. A trusted IT partner like Consilien IT Company can help your business stay protected from evolving social engineering attacks.
Consilien MSP provides services such as:
- Employee awareness training
- Security audits and risk assessments
- Implementation of MFA and advanced monitoring tools
- Real-time threat detection and response
- Policy and compliance support
By partnering with experienced professionals, you can save time, ensure appropriate settings, and be reassured that experts manage your cybersecurity.
FAQs: How to Protect Your Company from Social Engineering Attacks
1. What is a social engineering attack, and how does it work?
Social engineering attacks trick employees into revealing confidential information or taking harmful actions through fake messages, calls, or impersonations that exploit human trust and curiosity.
2. Why are social engineering attacks so effective?
Because they target people, not systems. Hackers prey on emotions like urgency or fear, causing employees to act quickly without verifying requests, which leads to major security breaches.
3. What are the most common types of social engineering attacks?
The main types include phishing, spear phishing, pretexting, baiting, tailgating, and quid pro quo all designed to trick employees into sharing sensitive data or granting access.
4. How can businesses protect themselves from social engineering attacks?
Companies should train employees regularly, enforce security policies, use multi-factor authentication, limit data access, and maintain strong technical defenses like email filters and antivirus tools.
5. How does Consilien IT Company help prevent social engineering threats?
Consilien provides tailored employee training, advanced monitoring systems, risk assessments, and compliance support to strengthen organizations’ defense against evolving social engineering attacks.
Takeaway
Social engineering will continue because it’s easier to influence human beings than technology. However, through proper awareness, policies, and technical controls, your business can prevent most of these attacks before they cause harm. Educate your staff, implement multi-factor authentication, maintain system security, and foster a culture of vigilance. Each employee is supposed to think twice before clicking, sharing or transferring anything. If you need assistance from a professional to enhance your cybersecurity posture, Consilien can help your organization with proven strategies and tailored protection frameworks. Our Security Awareness Training services are a great place to start for companies to stay protected from social engineering attacks.